IP Filter Validation policy to restrict access in Oracle API CS
IP white-list is a security feature often used for limiting and controlling access only to trusted users or applications.
Oracle API CS (Cloud Service) provides IP Filter Validation policy to control which IP Addresses can successfully send requests to the API.
The IP address originated by the client is received from the HTTPRequest. This policy checks if the address matches allowed or disallowed IP addressed configured as part of the policy. Upon finding a match, it takes appropriate action as configured. Nonstandard HTTP headers such as X-ProxyUser-Ip, X-Forwarded-For , or HTTP_X_CLUSTER_CLIENT_IP are not supported.
IP Filter Validation policy can be added in the request flow only. It can not be placed first in the flow. Other security polices must be placed before it.
Let’s see how to configure the IP Filter Validation policy using API CS console. To complete this task there should be API configured in API CS. If not, please go through the blog Creating an API in Oracle API Platform Cloud Service
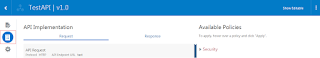
- Click on the TestAPI which was created in previous blog
- Click on API Implementation tab
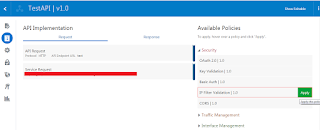
- In the Available Policies region, expand Security, hover over IP Filter Validation, and then click Apply
- From the Policy Dialog Enter below and click Next button:
- Your Policy Name (Optional): Enter a name for the policy
- Comments (Optional): Describe why we are applying the policy for this API
- Place after the following policy: Select the policy after which this policy is placed in the request flow
- From the IP Address Conditions list, select one of the following:
- Select PASS to pass the request if any of the IP Address conditions are met
- Select REJECT to reject the request to the API if any of the IP Address conditions are met
- In the IP Address field, select either IPv4 or IPv6
- In the Expression field, select the expression used to evaluate the addresses entered into the Value field. The following expressions are available:
- = (is equal to): Pass or Reject the equal IP address
- != (is not equal to): Pass or Reject the not equal IP address
- Inside: For example: 182.192.1.100-182.192.12.122
- Regex Match:. The Regex is made up of wildcard characters. If the IP of the host that is making the request to the API matches the wildcard, then it is passed or rejected. If no condition is evaluated to true, the opposite of the action gets executed. For example: 182.192.1.*
- CIDR Notation: Equal to an address included in the supplied CIDR notation expression. For Example: 182.192.12.123/24, which includes 182.192.12.0-182.192.12.255
- Click the + (Add a new condition) icon to add additional conditions
- Click Apply button



Excellent post. I was always checking this blog, and I’m impressed! Extremely useful info specially the last part, I care for such information a lot. I was exploring this particular info for a long time. Thanks to this blog my exploration has ended. 192.168
It is basic that we read blog entry deliberately. I am as of now done it and find this post is truly stunning. show my ip