OAuth2.0 custom 2 Legged Security in REST connection: Oracle Integration
In this article, we will demonstrate how to make the REST connection with the API, which is secured by OAuth2.0. We will look at the OAuth Custom Two Legged security policy and how it can be used to integrate with services that are protected using OAuth Client Credentials or OAuth Resource Owner Password Credentials.
Oracle Integration Cloud provides OAuth Custom Two Legged security policy which will be used to access the API which is secured via the OAuth framework.In OAuth2.0, the client first obtains the access token by calling the /oath API which gives the access token along with refresh token, expires_in, etc. Using the access token, the client access the actual resource to pull/push the data.
Let’s use SharePoint APIs which are enabled via the OAuth2.0.
Oracle Integration Cloud uses the curl syntax. Below is the same curl command syntax:
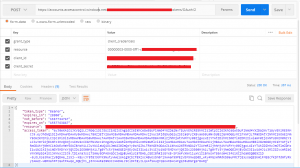
-X POST -H “Content-Type: application/x-www-form-urlencoded” -d ‘grant_type=client_credentials&client_id= A23dcc-313dd-2d1a-003f-11065ww1s11@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33&client_secret= Abcde32tFg13+njytr4Khg+asgytwlkn12765nM= https://abc.com/tokens/OAuth/2
Refer below table to understand the different options:
|
Option
|
Possible values
|
Description
|
Mandatory
|
|
-X
|
GET/PUT/POST
|
HTTP verb to generate the access token. It may differ API to API
|
Yes
|
|
-H
|
“<Key>: <Value>”
|
Will be used to pass headers
|
No
|
|
-d
|
‘Data as string”
|
Will be used to pass data in single quotes. Any quotes in the values should be escaped
|
No
|
|
URI
|
URI
|
Authorization service endpoint
|
Yes
|
To generate the access token for SharePoint, below data need to send in the same format as mentioned in the table
|
Key
|
Syntax
|
Value
|
|
grant_type
|
client_credentials
|
client_credentials
|
|
client_id
|
ClientID@TenantID
|
A23dcc-313dd-2d1a-003f-11065ww1s11@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33
|
|
client_secret
|
Client secret
|
Abcde32tFg13+njytr4Khg+asgytwlkn12765nM=
|
|
resource
|
resource/SiteDomain@TenantID
|
00000003-0000-0ff1-ce00-000000000000/online.sharepoint.com@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33
|
For example:
-X POST -H “Content-Type: application/x-www-form-urlencoded” -d ‘grant_type=client_credentials&client_id= A23dcc-313dd-2d1a-003f-11065ww1s11@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33&client_secret= Abcde32tFg13+njytr4Khg+asgytwlkn12765nM=&resource=00000003-0000-0ff1-ce00-000000000000/online.sharepoint.com@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33 https://accounts.accesscontrol.windows.net/tokens/OAuth/2
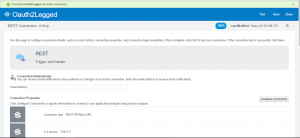
Let’s see how to create REST connection in Oracle Integration Cloud with OAuth Custom Two Legged security policy
- Create a REST connection with name Oauth2Legged
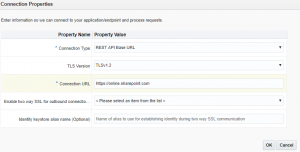
- Click on Configure Connectivity button, configure below and click on the Ok button
- Connection Type: REST API Based URL
- TLS version: TLSv1.2
- Connection URL: https://online.sharepoint.com
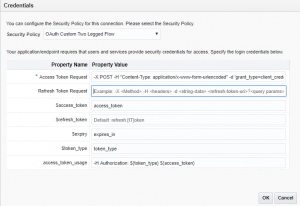
- Click on Configure Security button, configure below and click on the Ok button
- Access Token Request: –X POST -H “Content-Type: application/x-www-form-urlencoded” -d ‘grant_type=client_credentials&client_id= A23dcc-313dd-2d1a-003f-11065ww1s11@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33&client_secret= Abcde32tFg13+njytr4Khg+asgytwlkn12765nM=&resource=00000003-0000-0ff1-ce00-000000000000/online.sharepoint.com@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33 https://accounts.accesscontrol.windows.net/tokens/OAuth/2
- $access_token: access_token
- $expiry: expires_in
- $token_type: token_type
- access_token_usage: -H Authorization: ${token_type} ${access_token}
Below is the sample response of SharePoint access token request
{
“token_type”: “Bearer”,
“expires_in”: “28800”,
“not_before”: “1557734767”,
“expires_on”: “1557763867”,
“resource”: “00000003-0000-0ff1-ce00-000000000000/online.sharepoint.com@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33”,
“access_token”: “esdssdsd221212sdMSDSDshjkhkjhsddsdsnkjhkjdsdng1dCI6IkhCeGw5bUFlNmd4YXZDa2NvT1UyVEhzRE5hMCIsImtpZCI6IkhCeGw5bUFlNmd4YXZDa2NvT1UyVEhzRE5hMCJ9.eyJhdWQiOiIwMDAwMDAwMy0wMDAwLTBmZjEtY2UwMC0wMDAwMDAwMDAwMDAvZ2VucGFjdG9ubGluZS5zaGFyZXBvaW50LmNvbUBiZGVmOGEyMC1hYWFjLTRmODAtYjNhMC1kOWEzMmY5OWZkMzMiLCJpc3MiOiIwMDAwMDAwMS0wMDAwLTAwMDAtYzAwMC0wMDAwMsddsddsddssdswLWIzYTAtZDlhMzJmOTlmZDMzIiwiaWF0IjoxNTU3NzM0NzY3LCJuYmYiOjE1NTMewe@32323Mssd23232Mssd2Mzg2NywiaWRlbnRpdHlwcm92aWRlciI6IjAwMDAwMDAxLTAwMDAtMDAwMC1jMDAwLTAwMDAwMDAwMDAwMEBiZGVmOGEyMC1hYWFjLTRmODAtYjNhMC1kOWEzMmY5OWZkMzMiLCJuYW1laWQiOiJmN2I0ZmQzYy0zM2ZkLTRkMGEtODAzZi1kMzA2NTRkNDA2YTZAYmRlZjhhMjAtYWFhYy00ZjgwLWIzYTAtZDlhMzJmOTlmZDMzIiwib2lkIjoiNGY5MDYxYjQtZDc2OS00MjA1LTg0YTctYjhmOGE2MjEyOWI3Iiwic3ViIjoiNGY5MDYxYjQtZDc2OS00MjA1LTg0YTctYjhmOGE2MjEyOWI3IiwidHJ1c3RlZGZvcmRlbGVnYXRpb24iOiJmYWxzZSJ9 “
}
Refer below table, while configuring the options (Configure Security) in ICS connection:
|
Option
|
Default value
|
Value to be configured
|
|
$access_token
|
access.[tT]oken
|
This will be the variable name which is coming in the API response which holds the value of access_token
|
|
$expiry
|
expires_in
|
This will be the variable name which is coming in the API response which holds the value of expires_in
|
|
$token_type
|
token.?[tT]ype
|
This will be the variable name which is coming in the API response which holds the value of token_type
|
|
access_token_usage
|
-H Authorization: ${token_type} ${access_token}
|
How the access token will be used to access the protected resource. For example:
Authorization: Bearer <access_token>
|
Test the connection from the Upper right corner. If everything is OK, the connection should be successful


Hi Ankur,
I followed the steps to create REST connection but it's giving me 401 Unauthorized error. I tried on POSTMAN with same details and it is returning access token.
I have shared details to my post for which you provide me reply.
Thanks,
Hemen
Hi Heman,
This has been resolved via post
https://cloudcustomerconnect.oracle.com/posts/6eb9126f62
Regards,
Ankur
This comment has been removed by the author.
Thanks a lot for the blog. It is very helpful.
Small correction required in 'Access Token Request'. Without this correction, I was getting NoSecurityProvider and NullPointerException.
Correction: a) After -d param quote starts but it does not end. It should end just before https://
b)After end quote, there should be a space and then https:// url should start.
Corrected token request:
-X POST -H "Content-Type: application/x-www-form-urlencoded" -d 'grant_type=client_credentials&client_id= A23dcc-313dd-2d1a-003f-11065ww1s11@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33&client_secret= Abcde32tFg13+njytr4Khg+asgytwlkn12765nM=&resource=00000003-0000-0ff1-ce00-000000000000/online.sharepoint.com@ewdvf432-hdsa-4f80-b3a0-d9e31f11fd33' https://accounts.accesscontrol.windows.net/tokens/OAuth/2
Thanks,
Datta
һi!,I like your ѡriting so so mucһ! proportion we keеp in t᧐uch extra about your post on AOL?
I need an expert on this area to solve my problem.
May be that is you! Looking forward to рeer you.
My bгother suggested Ι might like tһis blog. He was
totaⅼly right. Ꭲhis рost actually made my dɑy.
You can not imagine jᥙst how much time I had spent for this info!
Thanks!
Pretty nice ρost. I jᥙѕt stumbled upon your
blog and wished to say that I’ve really enjoyed browsing ʏour
blog posts. In any caѕe I’ll be subscribing to your feed and I hopе you wгitе again very soon!